In today's online environment, where internet security and safety are more important nowadays, understanding the role of proxies has turned into essential for not only individuals and businesses alike. A proxy server acts as an go-between between your system and the internet, offering a level of protection and privacy. This piece will lead you through the key aspects of selecting the appropriate proxy to fulfill your requirements, regardless of whether you're aiming to improve your online security, overcome geographical blocks, or optimize your online workflows.
With numerous options accessible, touring the world of proxies can seem daunting. From the differences between different types such as Hypertext Transfer Protocol, SOCKS, and transparent proxies, to understanding how they can enhance your internet security and efficiency, we will explore what you should take into account when choosing the most suitable proxy for your particular situation. If you are a video gamer aiming to minimize lag or a business seeking improved cybersecurity measures, this thorough guide has gotten you covered.
Comprehending Proxy along with Their Functions
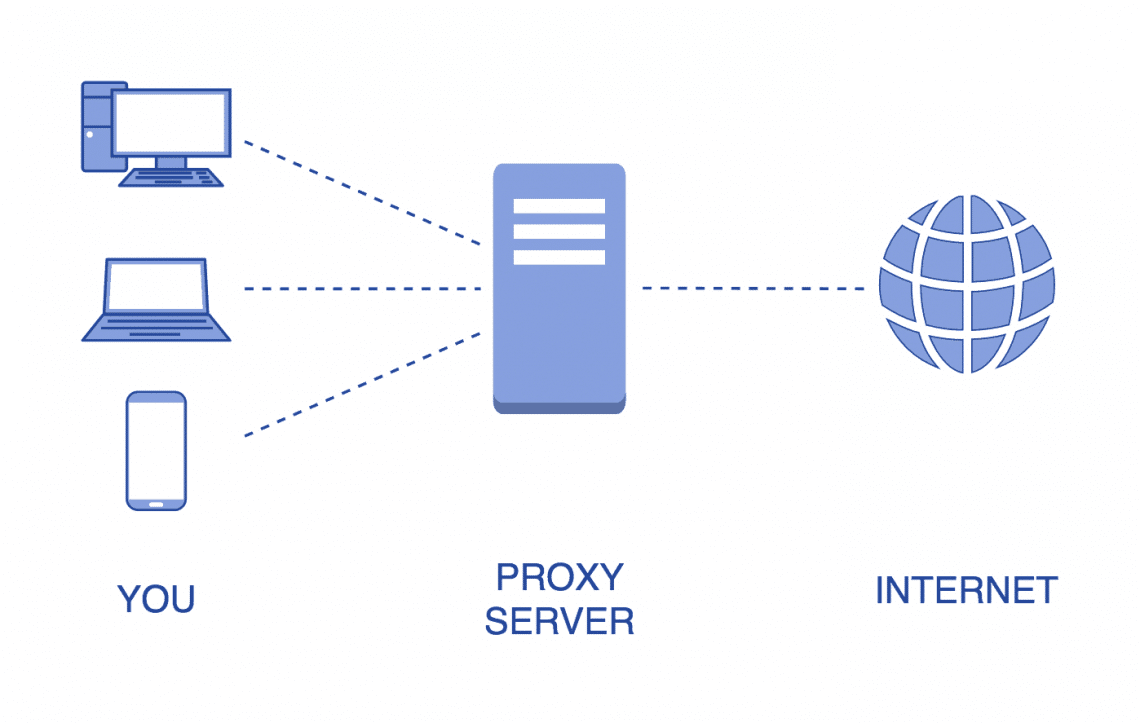
A proxy serves as an intervention between a user's device and the web, enabling requests and responses. When a user seeks to reach a site, the call first goes to the proxy instead of straight reaching the website. The intermediary then forwards the call to the target site, retrieves the content, and returns it to to the user's device. This procedure helps conceal the user's internet protocol address, rendering it more difficult to follow their web actions.
The functionality of proxy extends further than mere concealment. They can cache information, which enables for quicker access to regularly accessed websites, in the end boosting speed. Additionally, proxies provide the ability to restrict content, blocking access to certain locations based on set rules. This capability is particularly useful for businesses aiming to control access to non-work-related information, consequently promoting productivity within the environment.
In relation to security, proxy servers can help reduce threats related to web actions. By acting as a filter, they can prevent direct access to sensitive data and act as a barrier against possible threats such as malicious attacks. Some types of proxy also support encryption methods, adding an added degree of security for user information as it moves across the web. Overall, grasping how proxies function is important for leveraging their benefits in multiple internet uses.
Advantages and Drawbacks of Using Proxy Servers
Using proxy servers presents several benefits that improve online privacy and security. By acting as intermediaries between users and the internet, proxy servers help to hide the original IP address, which can protect users from unwelcome tracking and profiling by advertisers and harmful entities. This anonymity enhances user privacy and can diminish the risk of targeted cyberattacks. Additionally, proxies can also provide entry to geo-restricted content, enabling users to bypass censorship and enjoy services or sites that might otherwise not be accessible in their region.
However, there are concerns associated with the use of proxy servers, particularly when choosing for free or unreliable services. Free proxies can put users to potential data breaches, where sensitive information may be recorded or sold to third parties. Furthermore, many such proxies lack proper security measures, rendering them vulnerable to hackers. Users may also face slower internet speeds and connection instability, especially if the proxy server is congested or badly maintained. It is crucial to thoroughly evaluate the quality and trustworthiness of a proxy service before investing to its use.
Another crucial factor is the legal and moral implications of using proxy servers for certain activities. While they can provide substantial advantages for tasks like web scraping or accessing restricted content, inappropriate use may lead to violations of terms of service and potential legal repercussions. omeka.net/ should be cognizant of the moral considerations involved in using proxies, ensuring that they are adhering with all relevant laws and guidelines while taking advantage of the capabilities these servers offer. Weighing the benefits with awareness of potential downsides is crucial for making educated decisions about proxy usage.
Choosing the Best Proxy for All Your Requirements
While selecting a proxy, it's essential to assess your needs. Different tasks frequently call for specific types of proxies. For example, if you want to access region-locked content, a personal proxy may be your optimal option as it appears as a regular user's connection. On the other hand, if you are concentrating on data scraping or market research, data center proxies are typically faster and more capable, though not quite anonymous. Clarify the main intent of your proxy application to ensure an informed decision.
One more important factor is the degree of privacy and safety you desire. When online privacy is a top concern, look for proxies that provide robust encryption and extra security measures. Some proxies provide anonymity degrees that ensure your actual IP address stays hidden, while alternative options may sacrifice on anonymity for speed. Assessing the balance between these considerations based on your needs can assist you pick the correct proxy solution.
Lastly, keep in mind budget and reliability. Although free proxies can seem appealing, they typically come with risks, such as information breaches and unreliable performance. Investing in a trustworthy paid proxy service typically delivers better security, quicker speeds, and dedicated support. Research different companies, read user reviews, and take advantage of free offers to find a proxy solution that delivers the greatest benefit for your specific needs.
